In 2025, cybercriminals aren’t just targeting tech giants anymore—they’re going...Read More
The Ethical Hacking course is designed to be the starting point for a career in cybersecurity, equipping you with essential skills that lay the foundation for success in the field.
Group Enrollment with Friends and Colleagues | Get a quote

Offline and Online
24x7 Live Support
Weekday / Weekend
Choose Recon Cyber Security for the top ethical hacking course in Laxmi Nagar, Delhi. Our course offers expert-led training with a hands-on approach, ensuring you develop practical skills in ethical hacking techniques and cybersecurity tools. The tailored curriculum aligns with industry standards, giving you the knowledge and experience needed to excel in the field.
At Recon Cyber Security, we focus on enhancing your learning experience by providing access to real-world scenarios and advanced lab environments. This hands-on practice helps you refine your ethical hacking skills. Our instructors are industry professionals who offer valuable insights and the latest knowledge, helping you stay ahead in the fast-evolving world of cybersecurity. With personalized support and comprehensive resources, our course prepares you to confidently handle any cybersecurity challenges you may face.
Certified Ethical Hacking Course boost career growth in cybersecurity.
Opens doors to higher-paying and advanced cybersecurity roles.
Enhances employability and job security in the cybersecurity field.
Provides a competitive edge in the cybersecurity job market.

About Ethical Hacking Course
At Recon Cyber Security, we offer comprehensive ethical hacker training and certification to help you become a skilled ethical hacker. Our course covers everything from the basics of ethical hacking to advanced techniques used to identify and address security vulnerabilities. With our structured curriculum, hands-on labs, and expert instructors, you’ll gain the knowledge and skills needed to excel in the field. By the end of the course, you’ll be well-prepared to take the Certified Ethical Hacker (CEH) exam and earn a respected certification that enhances your career prospects.
Looking to advance your career in cybersecurity? Join the best ethical hacking courses in Delhi at Recon Cyber Security. Our classes provide top-notch training that equips you with practical skills and real-world knowledge in ethical hacking. Whether you’re aiming to become a certified ethical hacker or just want to learn more about ethical hacking, our courses offer in-depth instruction and hands-on experience. Enroll now to start your journey with the leading ethical hacker classes in Delhi and take a significant step towards becoming a certified ethical hacker.


★ ★ ★ ★ ★

★ ★ ★ ★ ★

★ ★ ★ ★ ★

★ ★ ★ ★ ★
Our Certified Ethical Hacker course in Laxmi Nagar, Delhi, provides you with an industry-recognized certification that opens doors to numerous opportunities in cybersecurity. This course is designed to equip you with the skills needed to think like a hacker and protect systems against cyber threats. With a focus on real-world scenarios, you’ll learn the latest techniques used by ethicalhackers to secure networks and systems. Earning your Certified Ethical Hacker certification will not only enhance your professional credentials but also make you a valuable asset in the cybersecurity field.
At Recon Cyber Security, our Ethical Hacker Training Course offers practical and in-depth learning that goes beyond the basics. You’ll dive into advanced topics like mobile hacking, network security, and vulnerability assessments, gaining hands-on experience that prepares you for real-world challenges. Whether you want to learn ethical hacking from scratch or enhance your current skills, our course is designed to meet your needs. Plus, with flexible schedules and competitive ethical hacking course fees, you can find the perfect course near you to start your journey in ethical hacking.

Ethical hacking, also known as penetration testing or white-hat hacking, involves legally breaking into systems to find security vulnerabilities. Unlike malicious hackers, ethical hackers work with permission and follow legal guidelines to help protect organizations from cyberattacks.
While basic programming knowledge can help, ethical hacking courses often start with fundamental cybersecurity concepts. You can pick up programming skills, like Python or JavaScript, as you progress through the ethical hacking course.
In the ethical hacking course, you will learn to defend against various cyber threats like phishing attacks, malware, ransomware, DDoS attacks, and SQL injections, using real-world ethical hacking techniques.
Yes, this ethical hacking course is designed to help you pass industry-recognized certifications like CEH (Certified Ethical Hacker) or OSCP (Offensive Security Certified Professional). It covers all the critical skills and tools required.
You will learn to use popular ethical hacking tools like Nmap, Metasploit, Burp Suite, Wireshark, and Kali Linux, which are essential for identifying and mitigating security vulnerabilities.
Yes, ethical hacking courses include legal and safe environments, such as virtual labs and Capture The Flag (CTF) challenges, where you can practice ethical hacking techniques without violating laws.
Ethical hackers identify weaknesses in networks, applications, and systems by performing penetration testing. This ethical hacking process helps organizations fix vulnerabilities before malicious hackers can exploit them.
Ethical hacking is in high demand due to the increasing number of cyber threats. Completing this ethical hacking course can lead to roles like penetration tester, security consultant, and cybersecurity analyst.
The time to become proficient in ethical hacking depends on your dedication and prior knowledge. With consistent effort, most students can gain a strong foundation in ethical hacking within 3-6 months.
Ethical hackers can work for cybersecurity firms, large corporations, or as freelance consultants. This ethical hacking course equips you with the skills to work in various environments, depending on your career goals.
Our Ethical Hacking classes in Laxmi Nagar, Delhi, offer flexible learning options to suit your schedule and learning style. Whether you prefer in-person sessions or an online ethical hacking course, we have you covered. Our courses are designed to help you learn hacking techniques and tools at your own pace, making it easier for you to balance your studies with other commitments. Whether you’re searching for a “hacking course near me” or an “online hacking course,” our flexible approach ensures you get the best training possible.
At Recon Cyber Security, we pride ourselves on being a leading Ethical Hacking Institute in Delhi, offering expert-led training that sets you up for success. Our certified instructors bring real-world experience to the classroom, guiding you through the latest ethical hacking techniques and the Certified Ethical Hacker v12 curriculum. You’ll gain hands-on experience and deep insights from professionals who have worked in the field, making our institute the perfect place to learn hacking and prepare for the Certified Ethical Hacker certification.
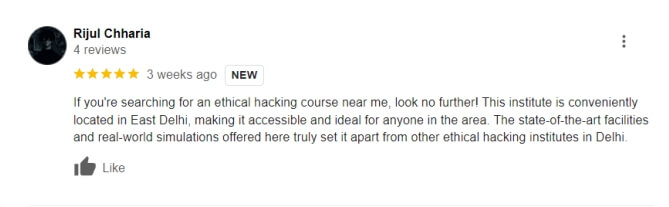
Searching for an “ethical hacking course near me”? Look no further! Located in the heart of Laxmi Nagar, Delhi, our institute offers a convenient and accessible location for aspiring ethical hackers. Whether you’re commuting from nearby or joining our ethical hacker training online, you’ll find that our courses are designed to be both accessible and effective. With the option to take classes in person or online, you can choose the learning environment that best suits your needs.
When you choose our Ethical Hacking Institute near you, you’re opting for a comprehensive and practical learning experience. We offer competitive fees, a curriculum that covers everything from the basics to advanced hacking techniques, and training available in both English and Hindi. Whether you’re aiming to earn the Certified Ethical Hacker cert or simply want to learn hacking to boost your career, our institute provides the resources and support you need to succeed.
In 2025, cybercriminals aren’t just targeting tech giants anymore—they’re going...Read More
As cyber threats evolve and become more sophisticated, blockchain technology...Read More
The dawn of 2024 brings groundbreaking advancements in 5G security...Read More
As cyber threats evolve, Zero Trust Architecture (ZTA) is emerging...Read More
At Recon Cyber Security, we are dedicated to providing world class training in the fields of cybersecurity, ethical hacking, and digital forensics. Based in Laxmi Nagar, Delhi, our mission is to empower individuals and organizations with the knowledge and skills needed to combat cyber threats in an increasingly digital world. Our expert-led courses, designed for beginners and professionals alike, offer hands-on experience and practical knowledge that directly translates to the field.