- Home
- »
- Beginner Diploma Course in Cyber Security | 6-Month Training Program in Delhi
6 Months
Diploma Course in Cyber Security
Beginner Diploma in Cyber Security: Learn cybersecurity fundamentals, ethical hacking, and network security basics.
- Course Duration: 6 Months
- Language: Hindi, English
- Course Delivery: Online, Offline
- Checkpoint Based Training
- 200 Gb Toolkit
Group Enrollment with Friends and Colleagues | Get a quote
Have any Questions?
Please leave your contact info and we will contact you back.
Learn the essential skills
Earn Recognized Certificate
Get ready for the next career
Master in Cyber Security
Our Workshops

Lingua University

Govt. School

Delhi University

MIET Jammu

IIT Roorkee

AIET Technologies

BITS Pilani

NIET College

IIT Delhi
About Us Recon Cyber Security Cyber Security Diploma
Recon Cyber Security Institute in Laxmi Nagar, Delhi, is a leading educational institution dedicated to empowering individuals with cutting-edge skills in cybersecurity. We offer a wide range of cyber security courses that cater to both beginners and professionals seeking to enhance their knowledge in the rapidly growing field of cybersecurity. Our expert-led training programs combine theoretical knowledge with practical experience, ensuring our students are well-equipped to tackle the ever-evolving challenges of the digital world.
At Recon Cyber Security, we believe in building the next generation of cybersecurity professionals. Our institute specializes in delivering top-notch cyber security courses designed to provide in-depth training in threat detection, risk management, and ethical hacking. With state-of-the-art labs and hands-on projects, we prepare students to face real-world security threats. Whether you are just starting out or looking to advance your career, Recon Cyber Security offers a learning environment that fosters growth and expertise in cybersecurity.
Our cyber security diploma course is one of the most comprehensive programs available in Delhi. Designed for aspiring cybersecurity professionals, this course covers all aspects of cybersecurity, from fundamental concepts to advanced techniques. Students will gain hands-on experience in network security, vulnerability assessment, and incident response. Recon Cyber Security offers the best diploma in cyber security, ensuring that our graduates are industry-ready and equipped with the skills to pursue a successful career. If you are looking for a cyber security diploma course in Delhi, our program provides the knowledge and experience needed to excel in this dynamic field.
6 Months Diploma Course Timelines
Material Included
- Interview Preparation
- 1,2,4 Hours Batches
- VA/PT Toolkit
- 6 Months Course Duration
- 1 Year Membership
- Hindi or English Language
- Online and Offline Training modes
- 7+ Years of Experice Trainer
Pre Requirements
- Students should have prior knowledge with Operation System such as : Windows 7, 8, 10, or 11 etc.
7 Levels of Cyber Security
Advanced Networking Course Modules
- Lesson 1 : Introduction to Advanced Networking
- Lesson 2 : Fundamentals of Networking
- Lesson 3 : OSI Model v/s TCP/IP Model
- Lesson 4 : MAC Address
- Lesson 5 : IP Addressing
- Lesson 6 : Subnetting
- Lesson 7 : Network Cabling
- Lesson 8 : Router Fundamentals
- Lesson 9 : Lab Configuration on Packet Tracer
- Lesson 10 : Router, Switch and PC Communication
- Lesson 11 : Routing Protocols
- Lesson 12 : Dynamic Routing
- Lesson 13 : DHCP
- Lesson 14 : NAT (Network Address Translation)
- Lesson 15 : V-LAN Configuration
- Lesson 16 : ACL (Access Control List)
- Lesson 17 : BGP Configuration
Linux Essentials Course Modules
- Lesson 1 : Introduction to Linux Evolution
- Lesson 2 : Linux Distribution
- Lesson 3 : Linux Embedded System
- Lesson 4 : Hardware Requirement
- Lesson 5 : Installing Linux
- Lesson 6 : OS Differences
- Lesson 7 : Open Software Application
- Lesson 8 : What is Open Source
- Lesson 9 : Desktop and server application
- Lesson 10 : Languages and tools
- Lesson 11 : Packages installas and repositories
- Lesson 12 : The Linux Environments
- Lesson 13 : Linux Desktop environments
- Lesson 14 : Linux shell and commands
- Lesson 15 : Managing softwares packages
- Lesson 16 : The command line
- Lesson 17 : Difference b/w shells
- Lesson 18 : Command line
- Lesson 19 : Command Usage
- Lesson 20 : Man Pages
- Lesson 21 : Directories and files
- Lesson 22 : Searching and Extracting Data from file
- Lesson 23 : Package installation in different Directory
- Lesson 24 : User account and groups
- Lesson 25 : Creating account from the shell
- Lesson 26 : Modifying and deleting account
- Lesson 27 : Working as root
- Lesson 28 : Managing file ownership and permission
Ethical Hacking Course Modules
- Lesson 1: Introduction to Ethical Hacking
- Lesson 2: Kali Linux Hands on Training
- Lesson 3: Reconnnaissance
- Lesson 4: Scanning Networks
- Lesson 5: Enumeration
- Lesson 6: System Hacking
- Lesson 7: Malware & Threats
- Lesson 8: Social Engineering
- Lesson 9: Denial of Service
- Lesson 10: Session Hijacking
- Lesson 11: Wireless Hacking
- Lesson 12: Mobile Hacking
- Lesson 13: Hacking Web-Application (with BurpSuite)
- Lesson 14: SQL Injection
- Lesson 15: Hacking Web Server
- Lesson 16: Sniffing / Sniffers
- Lesson 17: IDS, Firewall, Honeypot
- Lesson 18: Cryptography
- Lesson 19: Basics of Cloud Computing / Hacking
- Lesson 20: IoT Hacking
- Lesson 21: Basics of Penetration Testing
Python Programming Course Modules
- Lesson 1: Python An Overview
- Lesson 2: Python Variables & Data Types
- Lesson 3: Operators
- Lesson 4: Python Conditional Statements
- Lesson 5: Python Looping Concept
- Lesson 6: Python Control Statements
- Lesson 7: Python Data Type Casting
- Lesson 9: Python Number
- Lesson 10: Python String
- Lesson 11: Python List
- Lesson 12: Python Tuple
- Lesson 13: Python Dictionary
- Lesson 14: Python Sets
- Lesson 15: Python sys Lesson
- Lesson 16: Python OS Lesson
- Lesson 17: Python Function
- Lesson 18: Importing in Python
- Lesson 19: File Handling (Input/Output)
- Lesson 20: Exception Handling
- Lesson 21: OOPs Concepts
- Lesson 22: Multithreading
- Lesson 23: Python Mail Sending
- Lesson 24: Regular Expression
- Lesson 25: Python Web Scraping
- Lesson 26: Python Data Science
- Lesson 27: Introduction to Python Machine Learning
Penetration Testing Course Modules
- Lesson 1: How to plan your Penetration Testing
- Lesson 2: Scoping your Penetration Testing
- Lesson 3: Network & Web-Application
- Lesson 4: Scanning Vulnerability
- Lesson 5: Exploitation with Metasploit
- Lesson 6: Post-Exploitation
- Lesson 7: Pivoting Attack
- Lesson 8: Browser exploitation
- Lesson 9: In-Depth Password Attacks
- Lesson 10: Cracking / Solving CTF’s
- Lesson 11: Final Analysis
Web-application Penetration-Testing Course Modules
- Lesson 1: Introduction to Web-application Penetration-Testing
- Lesson 2: Finding Subdomains
- Lesson 3: Understanding HTTP
- Lesson 4: Access Control Flaws
- Lesson 5: Ajax Security
- Lesson 6: Authentication Flaws
- Lesson 7: Buffer Overflows
- Lesson 8: Code Quality
- Lesson 9: Concurrency Flaws
- Lesson 10: Cross-Site Scripting
- Lesson 11: Improper Error Handling
- Lesson 12: Injection Flaws
- Lesson 13: Denial of Service
- Lesson 14: Insecure Communication
- Lesson 15: Insecure Configuration
- Lesson 16: Insecure Storage
- Lesson 17: Malicious File Execution
- Lesson 18: Parameter Tampering
- Lesson 19: Challenge Online Platform
Mobile-App Penetration Testing Course Modules
- Lesson 1: Android Fundamentals
- Lesson 2: Introduction to Mobile-App Testing
- Lesson 3: Lab Setup
- Lesson 4: Android Architecture
- Lesson 5: APK File Structure
- Lesson 6: Reversing with APK tool / JADx-GUI
- Lesson 7: Reversing with MobSF
- Lesson 8: Static Analysis
- Lesson 9: Scanning Vulnerabilities with Drozer
- Lesson 10: Improper Platform Usage
- Lesson 11: Log Analysis
- Lesson 12: Insecure Storage
- Lesson 13: Insecure Communication
- Lesson 14: Hard Coding Issues
- Lesson 15: Insecure Authentication
- Lesson 16: Insufficient Cryptography
- Lesson 17: Code Tampering
- Lesson 18: Extraneous Functionality
- Lesson 19: SSL Pinning Attack
- Lesson 20: Intercepting The Network Traffic
- Lesson 21: Dynamic Analysis
- Lesson 22: Report Preparation
Training Options
Online Training Mode
- Weekdays and Weekend Classes
- 24x7 Learning assitance and Support
- Certificate after Completion
- Ebook Materials
- Every class session recordings available
- Instructure led Training
- Lifetime access
- Easy to Download material
Offline Training Mode
- Weekdays and Weekend Classes
- 24x7 Learning assitance and Support
- Certificate after Completion
- Ebook Materials
- Instructure led Training
- Live sessions
- Offline Training Access in every branch
Corporate Training Mode
- Weekdays and Weekend Classes
- 24x7 Learning assitance and Support
- Certificate after Completion
- Ebook Materials
- Live visit Training
- Professional Trainers
- Live Doubt sessions
Google Reviews (Over 3000+) ⭐⭐⭐⭐⭐ start ratings
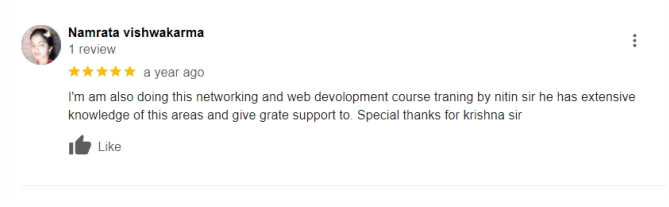
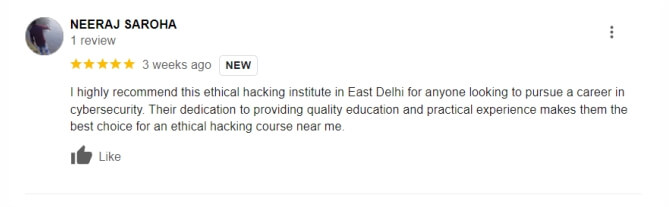
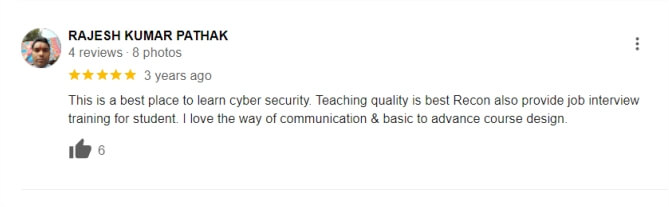

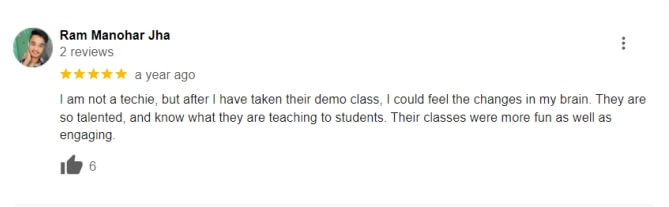
The Beginner Diploma in Cyber Security typically lasts for 6 months, offering comprehensive training in essential cybersecurity concepts. Our cyber security course in Delhi is designed to fit the schedules of aspiring professionals.
Our cyber security diploma course covers a range of topics, including network security, ethical hacking, data protection, and risk management. These fundamentals are crucial for anyone starting their journey in the field of cyber security.
Yes! The Beginner Diploma in Cyber Security is tailored for individuals with no prior experience. Our expert instructors at the cyber security institute in Delhi will guide you through the basics, ensuring you build a strong foundation in cyber security.
There are no specific prerequisites to join the Beginner Diploma in Cyber Security. A basic understanding of computers is helpful but not necessary. This makes it an excellent choice for anyone looking to start a career in cyber security.
Yes, upon successfully completing the Beginner Diploma in Cyber Security, you will receive a recognized certification. This certification from our cyber security institute in Delhi will enhance your resume and help you in your job search.
Flexible Networking Classes: Online and Offline Options
At Recon Cyber Security, we understand that flexibility is key to learning. That’s why we offer networking courses that are available both online and offline. Whether you prefer the convenience of learning from home or the interactive environment of a classroom, our networking courses in Delhi provide you with the options you need. Our flexible scheduling makes it easy for you to fit learning into your busy life.
Networking Fundamentals: Building a Strong Foundation
Our courses start with the essentials of IT networking basics, providing you with a strong foundation in the field. Understanding networking fundamentals is crucial for anyone looking to build a career in IT. Our introduction to computer networking course covers the basics, ensuring that you have a solid grasp of key concepts and skills. Start your journey with confidence at Recon Cyber Security.
Computer Networking Classes: Hands-On Experience and Real-World Projects
Gain practical, hands-on experience with our computer networking classes. We believe that learning by doing is the best way to master networking skills. That’s why our computer hardware networking course includes real-world projects that prepare you for the challenges you’ll face in the industry. Our expert instructors guide you through each step, providing the knowledge and support you need to succeed.
Introduction to Networking: Start Your Journey with Us
Begin your career in networking with our comprehensive introduction to networking course. Recon Cyber Security is the best networking institute for those looking to enter the field of network security. With our focus on practical skills and real-world applications, you’ll be well-prepared to take on roles in IT and network security. Whether you’re searching for a networking institute near you or looking for online options, Recon Cyber Security is your best choice for quality education and career success.
In 2025, cybercriminals aren’t just targeting tech giants anymore—they’re going...Read More
As cyber threats evolve and become more sophisticated, blockchain technology...Read More
The dawn of 2024 brings groundbreaking advancements in 5G security...Read More
As cyber threats evolve, Zero Trust Architecture (ZTA) is emerging...Read More




