In 2025, cybercriminals aren’t just targeting tech giants anymore—they’re going...Read More
Group Enrollment with Friends and Colleagues | Get a quote

Offline and Online
24x7 Live Support
Weekday / Weekend
The CTF Challenge course offered by Recon Cyber Security in Laxmi Nagar, Delhi, is an exciting and practical way to sharpen your cybersecurity skills. This course is designed to immerse you in real-world scenarios through Capture the Flag (CTF) challenges, where you’ll tackle a wide variety of security problems that simulate real cyberattacks. Whether you’re a beginner looking to build foundational skills or an experienced professional aiming to stay ahead of emerging threats, our CTF course provides a hands-on learning experience that encourages problem-solving and critical thinking in cybersecurity.
At Recon Cyber Security, we emphasize practical knowledge through interactive challenges, making you more confident in identifying and exploiting vulnerabilities in a controlled environment. Our expert instructors guide you through each step, from understanding basic security principles to solving complex issues, helping you grow into a proficient cybersecurity expert. By completing the course, you’ll not only enhance your technical abilities but also boost your confidence to participate in global CTF competitions, setting yourself apart in the competitive cybersecurity landscape.
CTF Challenge Course boost career growth in cybersecurity.
Opens doors to higher-paying and advanced cybersecurity roles.
Enhances employability and job security in the cybersecurity field.
Provides a competitive edge in the cybersecurity job market.

About Capture the Flag Challenges Course
At Recon Cyber Security in Laxmi Nagar, Delhi, our Linux Essentials Course includes exciting Capture the Flag (CTF) game training. This hands-on activity boosts your skills in an engaging way. Moreover, it involves solving challenges to capture flags, showing how cybersecurity works in real life. Whether you’re a beginner or want to improve, this training offers a great chance to practice and master CTF techniques in a safe setting
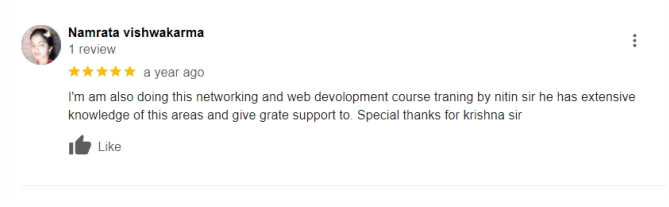
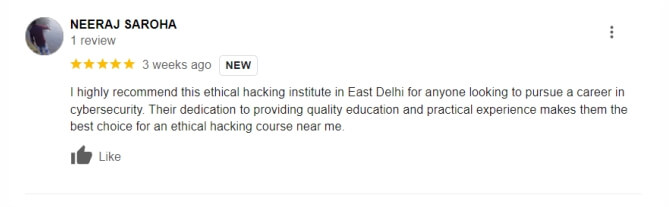
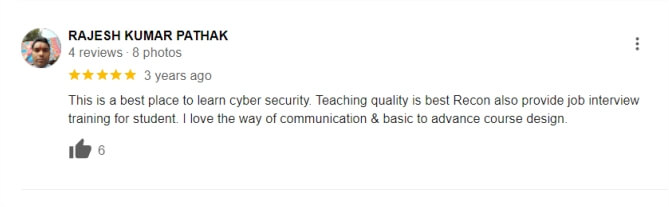

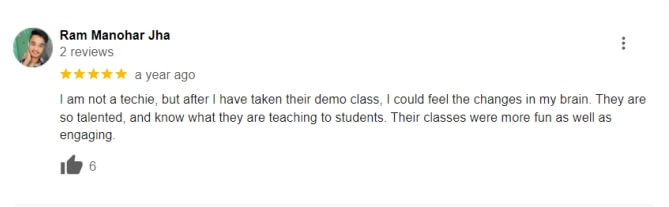

★ ★ ★ ★ ★

★ ★ ★ ★ ★

★ ★ ★ ★ ★

★ ★ ★ ★ ★
In our Linux Essentials Course in Laxmi Nagar, Delhi, we offer comprehensive “Flags for Capture the Flag” practical exercises designed to enhance your skills. These exercises simulate real-world hacking challenges, where you’ll practice catching the flag by solving complex puzzles and exploiting vulnerabilities. Our course provides hands-on experience with various flags for Capture the Flag, ensuring you understand how to approach and solve these challenges effectively.
Our course incorporates the “Catch the Flag Game,” where you tackle real-world hacking scenarios in a controlled environment. This game mimics actual cybersecurity situations, allowing you to practice catching the flag by identifying and exploiting security weaknesses. By engaging in these realistic scenarios, you’ll gain valuable insights into how real-world attacks occur and how to defend against them, enhancing your practical skills in cybersecurity.
The “CTF Training Course” at Recon Cyber Security offers a comprehensive learning path from basics to advanced techniques. Whether you’re new to Capture the Flag challenges or looking to refine your skills, our course covers everything you need. From understanding the fundamentals to mastering advanced CTF strategies, you’ll learn to excel in various capture the flag games, including stealing the flag and catching the flag, with practical exercises tailored to real-world applications.

A CTF challenge is a competitive cybersecurity exercise where participants solve real-world security problems or vulnerabilities to capture “flags” (pieces of code or data) hidden within systems.
CTF challenges simulate real-world attacks and defense scenarios, helping participants enhance skills like vulnerability detection, exploitation, cryptography, and reverse engineering in a hands-on environment.
You will face challenges in areas like web exploitation, reverse engineering, binary exploitation, forensics, cryptography, and network security, all designed to mimic real-world cyberattacks.
Both. CTF challenges can be done individually or in teams, depending on the competition format. This course will prepare you for both solo and collaborative problem-solving during events.
You will learn to use tools like Burp Suite, Wireshark, Metasploit, John the Ripper, Ghidra, and others to solve various types of CTF challenges across different categories.
Our Capture the Flag (CTF) challenges are designed to offer you hands-on experience and practical learning. These exercises mimic real-world hacking scenarios, helping you understand how to handle various security issues. By participating in our CTF challenges, you’ll gain skills in solving complex problems, finding vulnerabilities, and improving your cybersecurity techniques. Engage in these flags for capture the flag activities to enhance your practical knowledge and compete with peers in a dynamic environment.
Our CTF training course is tailored to accommodate various learning preferences, offering flexible options to fit your schedule. Whether you prefer online or in-person classes, our course provides a comprehensive curriculum that covers everything from the basics to advanced techniques. Learn how to excel in catch the flag game scenarios and become proficient in solving capture the flag puzzles. This course ensures that you are well-prepared for any steal the flag game challenge that comes your way.
Mastering the art of catching the flag involves understanding and applying various strategies and techniques. Our training focuses on teaching effective methods to tackle capture the flag game challenges. You’ll learn how to approach problems systematically, use the right tools, and employ creative solutions to succeed. These strategies will be invaluable as you progress through the CTF training course and face more complex flags for capture the flag scenarios.
For those looking to push their skills to the next level, our advanced capture the flag game offers an exciting challenge. This course is designed to test your limits and expand your abilities with more difficult and intricate problems. By engaging in high-level catch the flag game exercises, you will refine your expertise and gain a deeper understanding of capture the flag techniques. Prepare yourself to excel in the most demanding CTF training course environments and stay ahead in the world of cybersecurity.
In 2025, cybercriminals aren’t just targeting tech giants anymore—they’re going...Read More
As cyber threats evolve and become more sophisticated, blockchain technology...Read More
The dawn of 2024 brings groundbreaking advancements in 5G security...Read More
As cyber threats evolve, Zero Trust Architecture (ZTA) is emerging...Read More
At Recon Cyber Security, we are dedicated to providing world class training in the fields of cybersecurity, ethical hacking, and digital forensics. Based in Laxmi Nagar, Delhi, our mission is to empower individuals and organizations with the knowledge and skills needed to combat cyber threats in an increasingly digital world. Our expert-led courses, designed for beginners and professionals alike, offer hands-on experience and practical knowledge that directly translates to the field.