In 2025, cybercriminals aren’t just targeting tech giants anymore—they’re going...Read More
Enroll in the Professional Diploma in Cyber Security at Recon Cyber Security and advance your career with hands-on skills and expert knowledge.
Group Enrollment with Friends and Colleagues | Get a quote









Recon Cyber Security Institute in Laxmi Nagar, Delhi, is a top institution for learning modern security skills. It offers a variety of cybersecurity courses, such as ethical hacking, penetration testing, bug hunting, AWS cloud computing, IoT security, and cyber forensics. Additionally, the professional diploma combines theory with hands-on practice to help students build careers in this fast-changing field.
At Recon Cyber Security, we specialize in developing future cybersecurity experts by offering in-depth training in threat detection, risk management, and ethical hacking. Our programs are designed to be practical, with state-of-the-art labs and real-world projects to ensure students can tackle today’s cybersecurity challenges. Whether you are interested in penetration testing, AWS cloud computing, or IoT security, we provide a comprehensive learning experience.
Our Professional Diploma in Cyber Security is one of the most well-rounded programs in Delhi, covering fundamental concepts as well as advanced techniques. Students will gain expertise in areas like network security, vulnerability assessment, and incident response. If you are searching for a top-tier cyber security diploma course in Delhi, our program will provide you with the knowledge and practical experience necessary to excel in the industry.
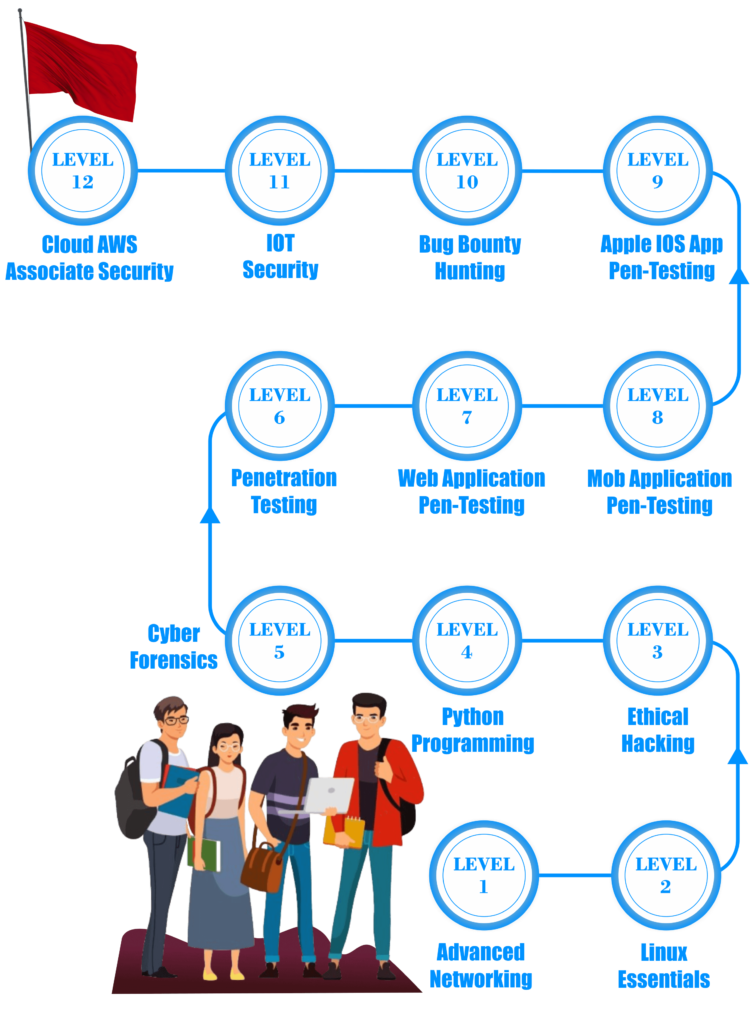
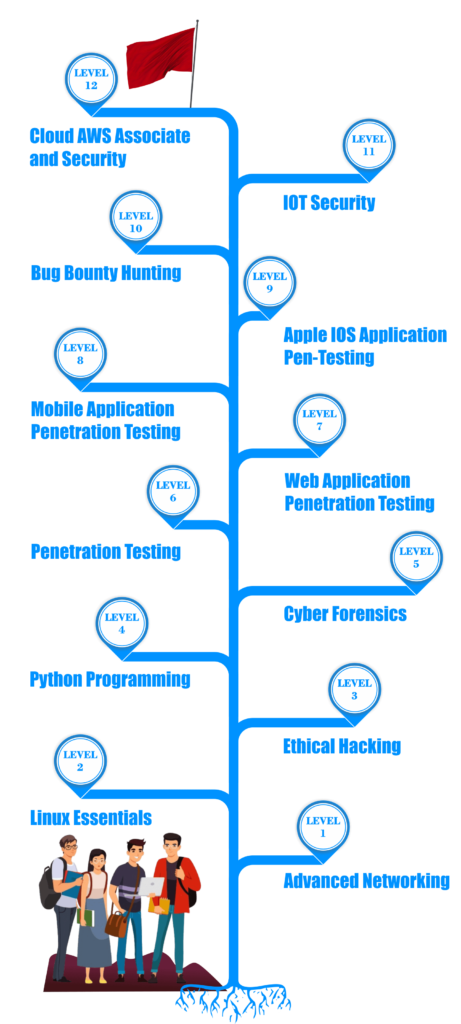

The Diploma Course in Cyber Security at Recon Cyber Security typically lasts for 6 to 12 months, depending on whether you choose a full-time or part-time schedule. You can enroll at our cyber security institute in Delhi for flexible class timings.
The cyber security diploma course covers a wide range of topics, including network security, ethical hacking, malware analysis, penetration testing, and more. It’s designed to give you a comprehensive understanding of cyber security practices.
Yes, the cyber security diploma course at Recon Cyber Security is beginner-friendly. Whether you’re new to cyber security or have some prior knowledge, this course is structured to build your skills from the ground up.
Yes, after completing the Diploma Course in Cyber Security, Recon Cyber Security offers placement assistance. We have tie-ups with various companies, especially in Delhi, and provide support to help you find a job in the cyber security industry.
Yes, at Recon Cyber Security, we offer both online and classroom training. If you’re searching for a cyber security institute near me or prefer studying from home, our online courses provide flexibility while maintaining the same high-quality education.
At Recon Cyber Security, we understand that flexibility is key to learning. That’s why we offer networking courses that are available both online and offline. Whether you prefer the convenience of learning from home or the interactive environment of a classroom, our networking courses in Delhi provide you with the options you need. Our flexible scheduling makes it easy for you to fit learning into your busy life.
Our courses start with the essentials of IT networking basics, providing you with a strong foundation in the field. Understanding networking fundamentals is crucial for anyone looking to build a career in IT. Our introduction to computer networking course covers the basics, ensuring that you have a solid grasp of key concepts and skills. Start your journey with confidence at Recon Cyber Security.
Gain practical, hands-on experience with our computer networking classes. We believe that learning by doing is the best way to master networking skills. That’s why our computer hardware networking course includes real-world projects that prepare you for the challenges you’ll face in the industry. Our expert instructors guide you through each step, providing the knowledge and support you need to succeed.
Begin your career in networking with our comprehensive introduction to networking course. Recon Cyber Security is the best networking institute for those looking to enter the field of network security. With our focus on practical skills and real-world applications, you’ll be well-prepared to take on roles in IT and network security. Whether you’re searching for a networking institute near you or looking for online options, Recon Cyber Security is your best choice for quality education and career success.
In 2025, cybercriminals aren’t just targeting tech giants anymore—they’re going...Read More
As cyber threats evolve and become more sophisticated, blockchain technology...Read More
The dawn of 2024 brings groundbreaking advancements in 5G security...Read More
As cyber threats evolve, Zero Trust Architecture (ZTA) is emerging...Read More
At Recon Cyber Security, we are dedicated to providing world class training in the fields of cybersecurity, ethical hacking, and digital forensics. Based in Laxmi Nagar, Delhi, our mission is to empower individuals and organizations with the knowledge and skills needed to combat cyber threats in an increasingly digital world. Our expert-led courses, designed for beginners and professionals alike, offer hands-on experience and practical knowledge that directly translates to the field.