In 2025, cybercriminals aren’t just targeting tech giants anymore—they’re going...Read More
Group Enrollment with Friends and Colleagues | Get a quote

Offline and Online
24x7 Live Support
Weekday / Weekend
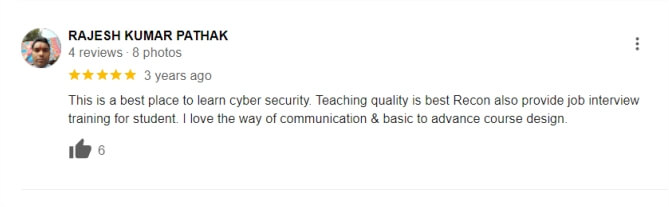
The Bug Bounty Hunting course at Recon Cyber Security is designed to equip you with the skills to identify and report security vulnerabilities in real-world applications. This comprehensive course covers everything from basic hacking concepts to advanced bug hunting techniques, ensuring that you understand how to find weaknesses in web, mobile, and network systems. You’ll learn how to responsibly disclose vulnerabilities, analyze security risks, and engage with bug bounty programs across leading platforms.
With hands-on training and expert guidance, this course prepares you for the fast-growing world of ethical hacking and bug bounty hunting. Whether you’re a beginner or an experienced professional, our course will help you enhance your skills in penetration testing, vulnerability assessment, and exploit development. Upon completion, you’ll be ready to participate in bug bounty programs, offering a great way to gain recognition in the cybersecurity community and potentially earn rewards for your findings.
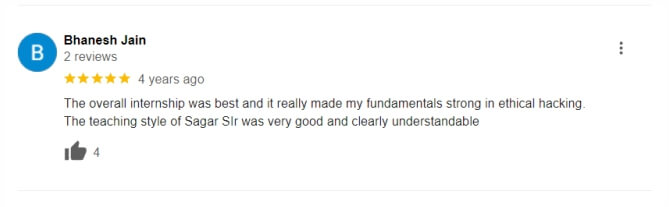
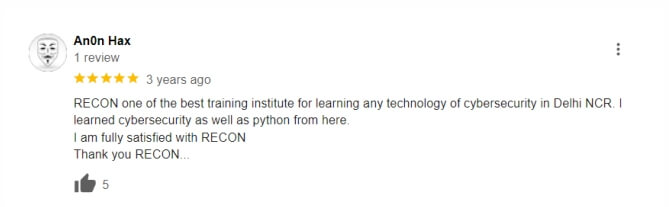
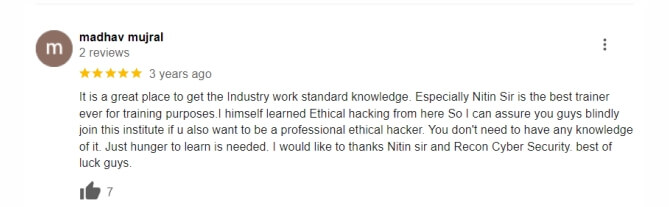
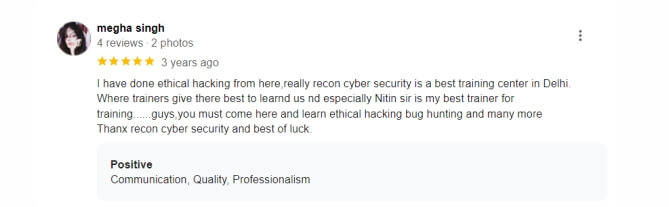
Bug Hunting Course boost career growth in cybersecurity.
Opens doors to higher-paying and advanced cybersecurity roles.
Enhances employability and job security in the cybersecurity field.
Provides a competitive edge in the cybersecurity job market.

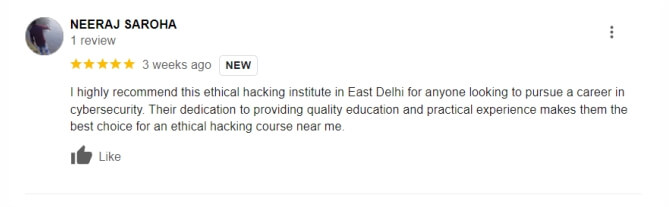
Our bug bounty hunting training at Recon Cyber Security in Laxmi Nagar, Delhi, is ideal for both beginners and advanced learners. Additionally, this bug hunting course includes everything from basic concepts to advanced techniques, giving you a solid foundation. Through hands-on practice, you will also learn how to identify and exploit vulnerabilities effectively. Moreover, it’s perfect for those starting fresh and equips you to tackle advanced challenges, making it the best choice for anyone pursuing bug bounty hunting.

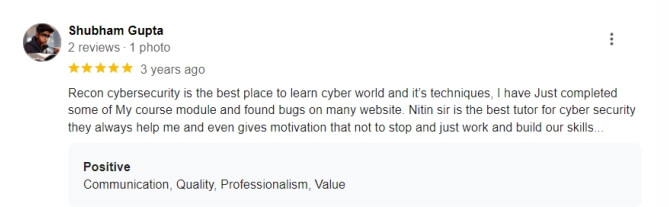
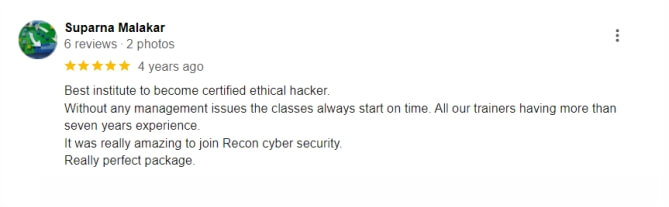

★ ★ ★ ★ ★

★ ★ ★ ★ ★

★ ★ ★ ★ ★

★ ★ ★ ★ ★
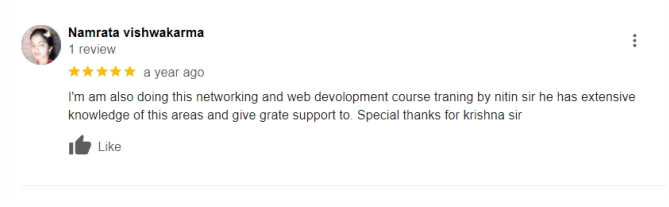
Our Bug Hunting Course lets you learn from industry experts with real-world experience. It is ideal for both beginners and professionals wanting to improve their skills. Through hands-on training, you’ll master practical techniques from top experts. Furthermore, our guidance helps you spot vulnerabilities and enhance your bug bounty skills with ease.
Our Bug Bounty Course Online provides flexible learning options tailored to fit your schedule. Whether you’re a busy professional or a student, our online course format allows you to learn at your own pace from anywhere. The course covers everything from basic bug bounty principles to advanced strategies, ensuring you have access to a comprehensive learning experience. Enroll today and start your journey towards becoming a skilled bug bounty hunter with the convenience of online learning.
Our Bug Bounty Course stands out as the best course for bug bounty enthusiasts, offering an industry-recognized certification upon completion. This certification validates your skills and knowledge in the field of bug bounty hunting, making you a valuable asset to potential employers or clients. The course provides a complete learning path, from introductory concepts to advanced techniques, ensuring you’re well-prepared for real-world challenges. Gain the credentials and expertise needed to excel with our top-rated bug bounty training program.

Bug hunting is the practice of finding and reporting security vulnerabilities in software, websites, or applications. It helps developers patch vulnerabilities before they can be exploited, improving overall cybersecurity.
Yes, this course covers how to join bug bounty platforms like HackerOne and Bugcrowd, as well as how to submit detailed vulnerability reports to earn rewards from companies.
You will focus on common vulnerabilities such as cross-site scripting (XSS), SQL injection, insecure authentication, and logic flaws, which are often targeted in bug bounty programs.
Yes, you will learn to use tools like Burp Suite, OWASP ZAP, and automated scanners to identify potential bugs in web applications and software systems during your bug hunting activities.
This course emphasizes the importance of ethical hacking principles, such as only testing on authorized systems, obtaining permission before testing, and responsibly reporting vulnerabilities to the appropriate parties.
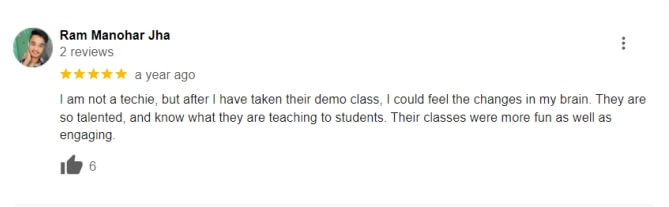
Our Bug Bounty Training offers hands-on, practical experiences that mirror real-world scenarios. You’ll gain valuable skills through live exercises and simulations that prepare you to tackle real vulnerabilities. This training is designed to help you understand the complexities of bug hunting and apply your knowledge effectively in various situations. Whether you’re looking for an advanced bug bounty course or a complete bug bounty course, this program ensures that you gain practical insights and real-world applications to enhance your skills.
Our Bug Bounty Complete Course provides a comprehensive learning experience that covers everything from basic to advanced techniques. This all-inclusive training program is ideal for those who want to master the art of bug hunting. With in-depth modules and expert guidance, you’ll explore every aspect of bug bounty hunting. Whether you are interested in a bug bounty full course or an online course, this complete training package is your gateway to becoming a proficient bug bounty hunter.
If you’re new to ethical hacking, our Bug Bounty Course for Beginners is the perfect place to start. This course is designed to introduce you to the fundamental concepts of bug bounty hunting and guide you through the initial steps of your journey. From learning the basics to understanding essential tools, this course will lay a solid foundation for your bug bounty learning path. It’s the best course for bug bounty enthusiasts who want to begin their ethical hacking journey with confidence.
Our Bug Bounty Course is recognized as one of the best bug bounty courses available. With proven success and a track record of producing skilled bug bounty hunters, this course offers expert guidance and unparalleled training. We provide a well-structured bug bounty master class that combines theoretical knowledge with practical experience. Whether you are looking for the best course for bug bounty or a comprehensive online course, our training is designed to deliver exceptional results and ensure you reach your goals.
In 2025, cybercriminals aren’t just targeting tech giants anymore—they’re going...Read More
As cyber threats evolve and become more sophisticated, blockchain technology...Read More
The dawn of 2024 brings groundbreaking advancements in 5G security...Read More
As cyber threats evolve, Zero Trust Architecture (ZTA) is emerging...Read More
At Recon Cyber Security, we are dedicated to providing world class training in the fields of cybersecurity, ethical hacking, and digital forensics. Based in Laxmi Nagar, Delhi, our mission is to empower individuals and organizations with the knowledge and skills needed to combat cyber threats in an increasingly digital world. Our expert-led courses, designed for beginners and professionals alike, offer hands-on experience and practical knowledge that directly translates to the field.