In 2025, cybercriminals aren’t just targeting tech giants anymore—they’re going...Read More
Master Diploma in Cyber Security: Advanced training in ethical hacking, threat analysis, and cybersecurity strategies.
Group Enrollment with Friends and Colleagues | Get a quote









Recon Cyber Security Institute in Laxmi Nagar, Delhi, is a leading institution dedicated to providing advanced education and training in the field of cybersecurity. We offer a Master Diploma in Cyber Security that equips individuals with the most cutting-edge skills needed to excel in the ever-evolving world of digital security. Whether you’re a seasoned professional or looking to upgrade your expertise, our program is designed to provide comprehensive knowledge combined with hands-on experience, ensuring students are prepared to tackle the latest cybersecurity threats.
Our Master Diploma in Cyber Security focuses on developing proficiency in critical areas such as ethical hacking, penetration testing, bug hunting, Apple iOS testing, API testing, and malware analysis. In addition to theoretical training, we emphasize real-world application through CTF (Capture The Flag) challenges and practical labs. Our expert-led curriculum is tailored to provide in-depth knowledge on threat detection, risk management, and the latest tools used in the cybersecurity industry.
At Recon Cyber Security, we are committed to building the next generation of cybersecurity professionals. Our state-of-the-art infrastructure and hands-on projects ensure students gain practical experience in areas such as network security, vulnerability assessment, and incident response. By completing our Master Diploma course, you will not only enhance your technical expertise but also be industry-ready, equipped with the skills necessary to secure high-demand roles in the cybersecurity landscape.
Recon Cyber Security’s Master Diploma in Cyber Security is one of the most comprehensive programs in Delhi, providing everything from basic cybersecurity principles to advanced hacking techniques. Whether you’re interested in ethical hacking, penetration testing, or learning about API security, our program offers the depth and expertise required to excel in this fast-growing field. If you’re seeking to become an expert in cybersecurity, our Master Diploma is the perfect choice to propel your career forward.
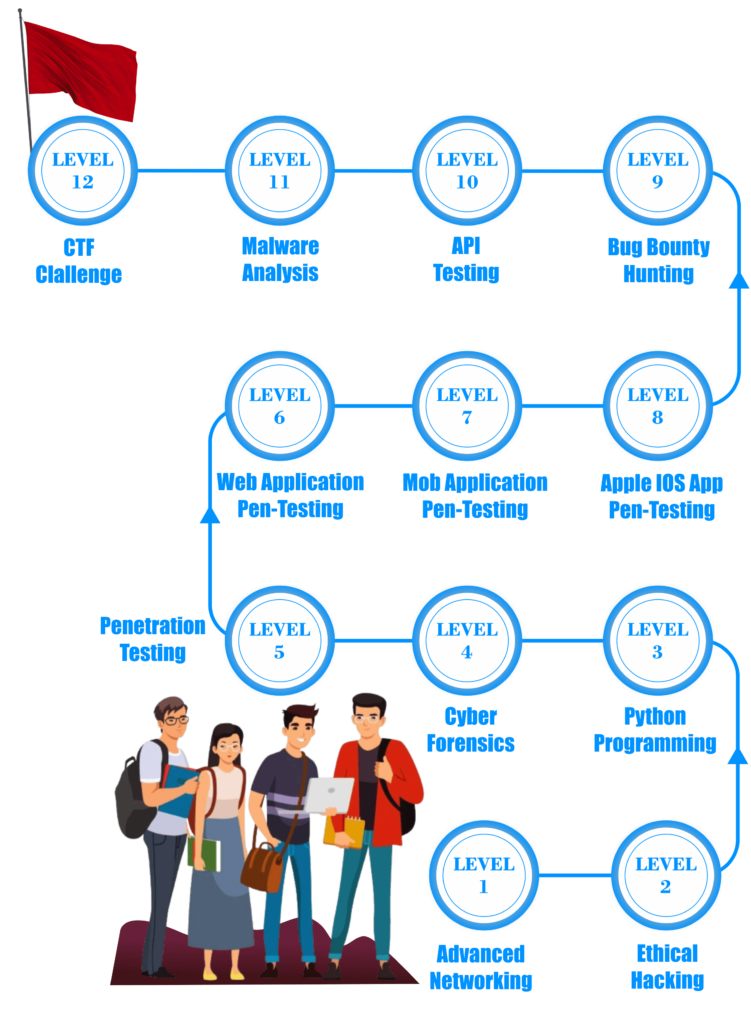
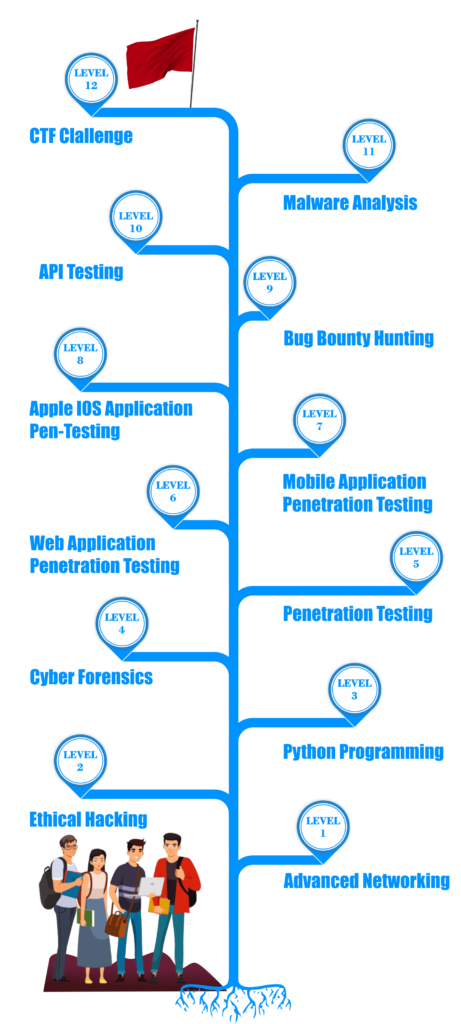

In the Expert Diploma Course in Cyber Security, you will learn advanced techniques for securing networks, performing penetration testing, and understanding cyber threats. This cyber security course in Delhi covers real-world scenarios to help you protect systems from sophisticated attacks.
Unlike basic courses, the cyber security diploma course at Recon Cyber Security is designed for professionals looking to master advanced skills in malware analysis, ethical hacking, and network security. It’s offered by a top-rated cyber security institute in Delhi, providing hands-on training.
This cyber security course is best suited for individuals with some basic knowledge of IT or networking. However, if you’re new to the field, you can still join as our instructors at Recon Cyber Security will guide you from the basics to expert level.
Yes, while our cyber security institute in Delhi offers in-person classes, we also provide online options. You can learn advanced cybersecurity techniques from anywhere, just search for a cyber security institute near me, and you will find our flexible online courses.
After completing this cyber security diploma course, you can pursue roles like Cyber Security Analyst, Ethical Hacker, or Network Security Expert. This cyber security course in Delhi is designed to open doors to high-paying jobs in the cybersecurity field.
At Recon Cyber Security, we know that flexibility is crucial for effective learning. Therefore, we offer networking courses both online and offline. You can choose to learn from home or join a classroom for an interactive experience. Additionally, our flexible schedules help you fit learning into your busy routine
Our courses start with the essentials of IT networking basics, providing you with a strong foundation in the field. Understanding networking fundamentals is crucial for anyone looking to build a career in IT. Our introduction to computer networking course covers the basics, ensuring that you have a solid grasp of key concepts and skills. Start your journey with confidence at Recon Cyber Security.
Gain practical, hands-on experience with our computer networking classes. We believe that learning by doing is the best way to master networking skills. That’s why our computer hardware networking course includes real-world projects that prepare you for the challenges you’ll face in the industry. Our expert instructors guide you through each step, providing the knowledge and support you need to succeed.
Begin your career in networking with our comprehensive introduction to networking course. Recon Cyber Security is the best networking institute for those looking to enter the field of network security. With our focus on practical skills and real-world applications, you’ll be well-prepared to take on roles in IT and network security. Whether you’re searching for a networking institute near you or looking for online options, Recon Cyber Security is your best choice for quality education and career success.
In 2025, cybercriminals aren’t just targeting tech giants anymore—they’re going...Read More
As cyber threats evolve and become more sophisticated, blockchain technology...Read More
The dawn of 2024 brings groundbreaking advancements in 5G security...Read More
As cyber threats evolve, Zero Trust Architecture (ZTA) is emerging...Read More
At Recon Cyber Security, we are dedicated to providing world class training in the fields of cybersecurity, ethical hacking, and digital forensics. Based in Laxmi Nagar, Delhi, our mission is to empower individuals and organizations with the knowledge and skills needed to combat cyber threats in an increasingly digital world. Our expert-led courses, designed for beginners and professionals alike, offer hands-on experience and practical knowledge that directly translates to the field.